DNSSight links each DNS query back to the exact device, user, and process—out-of-band, with zero impact on performance.


Most security stacks already include DNS security and protective controls,
yet alerts still arrive without clear ownership.
Investigations stall because DNS must be stitched to device, user, and process by hand across DHCP, VPN, identity, and EDR. Most teams keep raw DNS out of SIEM; signals sit unused or delayed.
Risk remains.

Ownership is set at ingestion: device, user, process.
Cross-checking DHCP, VPN, IdP, and EDR is no longer manual.
Pilots observed an average ROI increase of ~18%, driven by reduced ingest and shorter time-to-decision.
Ownership is set at ingestion: device, user, process.
Cross-checking DHCP, VPN, IdP, and EDR is no longer manual.
Pilots observed an average ROI increase of ~18%, driven by reduced ingest and shorter time-to-decision.
Maps each FQDN to the definitive host, active identity, and process. Turns DNS alerts into accountable incidents and shortens the step from signal to decision.
Names the exact user behind VPN egress for every DNS event. Keeps attribution intact across shared egress, session churn, and remote work.
Builds a single, ordered record linking device, user, process, and time. Exports cleanly to SIEM or ITSM and audit so evidence travels without rework.
.avif)
.avif)
Safely tests real detections against firewall, proxy, and DNS controls. Delivers per control pass or fail in minutes. Provides continuous proof of what is actually blocked without changing topology.
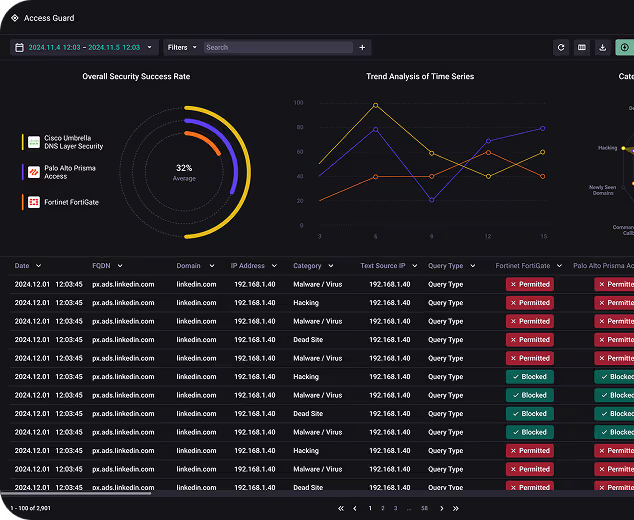
Safely tests real detections against firewall, proxy, and DNS controls. Delivers per control pass or fail in minutes. Provides continuous proof of what is actually blocked without changing topology.
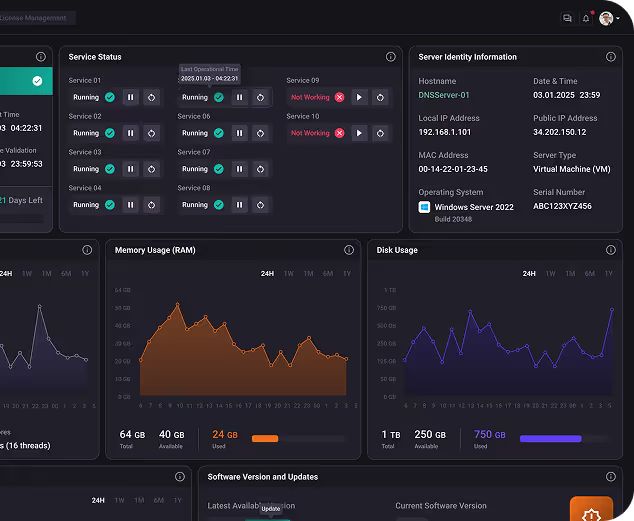
Do full investigations in DNSSight or, alert to SIEM, export to ITSM only for retention, routing, or reporting needs.
DNS Visibility complements protective DNS service providers, DNS security tools, URL filtering, and DNSSEC protection.
It adds the attribution layer these systems are not designed to provide without requiring remapping or replacing network tools.
DNS Visibility complements protective DNS service providers, DNS security tools, URL filtering, and DNSSEC protection.
It adds the attribution layer these systems are not designed to provide without requiring remapping or replacing network tools.
DNS Visibility complements protective DNS service providers, DNS security tools, URL filtering, and DNSSEC protection.
It adds the attribution layer these systems are not designed to provide without requiring remapping or replacing network tools.



Identify the real user and device inside GlobalProtect sessions; enrich firewall alerts with first-seen, frequency, and peer activity; forward context to Cortex XSIAM or your SIEM.
Typical setup ~15 minutes.
Operates out-of-band; no inline components. Raw DNS can stay at the resolvers, DDI, or data lake to investigate and close cases.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Alerts without owners drain time and budget. DNSSight makes DNS accountable by attaching device, identity, and process to critical moments. Decisions arrive faster, storage grows slower, posture strengthens.

Request a personalized DNSSight demo and see why thousands of organizations trust our DNS security platform to gain visibility, enforce control, and reduce risk—effortlessly.




